In today’s rapidly evolving digital landscape, The Five Essential Stages of Cyber Security have become critical for every organization aiming to protect sensitive data, networks, and systems from cyber threats. Understanding The Five Essential Stages of Cyber Security allows businesses to build a strong defense against potential attacks. Below, we explore each stage in detail and how it contributes to a robust cybersecurity framework.
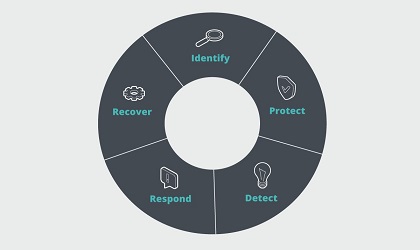
The Five Essential Stages of Cyber Security:
- Identification
The first stage is identifying the assets, systems, and data that need protection. This involves a thorough assessment of your organization’s IT infrastructure to identify vulnerabilities and understand potential threats. By cataloging all critical assets and mapping network interconnections, you can gain insights into weak points that attackers may exploit. Effective identification, as the first step in The Five Essential Stages of Cyber Security, sets the foundation for a secure network and prepares you for potential threats.
- Protection
After identification, the next phase of Cyber Security is protection. In this stage, organizations implement protective measures to prevent unauthorized access, ensure data integrity, and maintain confidentiality. Strategies like installing firewalls, using encryption, and employing multi-factor authentication are key elements of protection within The Five Essential Stages of Cyber Security.
- Detection
Even with robust protections in place, threats may still bypass defenses. That’s why detection is the third phase in the five stages of cyber security. Early detection allows organizations to respond swiftly, minimizing damage from cyber incidents. By implementing tools like intrusion detection systems (IDS) and Security Information and Event Management (SIEM), businesses can effectively identify potential breaches as part of The Five Essential Stages of Cyber Security.
- Response
The fourth stage in The Five Essential Stages of Cyber Security is Response. When a security breach is detected, the response stage focuses on managing the incident to contain and mitigate the threat. A well-coordinated response strategy can significantly reduce the impact of a cyberattack and prevent further damage.
An effective response strategy should include a detailed incident response plan, clearly defining roles and responsibilities for all team members. Organizations must establish communication protocols to inform key stakeholders and legal authorities when necessary. Containment measures should be implemented to isolate affected systems, and forensic analysis should be conducted to determine the root cause of the breach. By having a proactive response plan, companies can address cyber incidents efficiently and limit the damage.
- Recovery
The fifth and final stage in The Five Essential Stages of Cyber Security is Recovery. Once the threat has been neutralized, the recovery stage focuses on restoring affected systems and resuming normal operations. This stage also includes reviewing the incident to extract valuable lessons and strengthen security practices.
Recovery strategies typically involve restoring data from secure backups, repairing or replacing compromised systems, and reinforcing security measures to prevent similar incidents in the future. A successful recovery plan ensures business continuity and enables the organization to resume operations with minimal disruption. Conducting a post-incident review will provide insights into how the incident was managed and help refine the overall security strategy.
Continuous Improvement in Cybersecurity
In addition to implementing The Five Essential Stages of Cyber Security, organizations should continuously evaluate and enhance their cybersecurity strategies. As cyber threats evolve, so must the defenses. Leveraging advanced technologies like artificial intelligence (AI) and machine learning (ML) can provide deeper insights into threat patterns and automate responses to emerging attacks. Regular security audits, employee training programs, and adopting a proactive security mindset are crucial for maintaining a resilient defense.
Conclusion
The Five Essential Stages of Cyber Security—Identification, Protection, Detection, Response, and Recovery—are crucial for safeguarding digital assets and minimizing the risk of cyberattacks. By regularly updating security practices, monitoring threats, and adapting to new challenges, organizations can maintain a resilient cybersecurity framework. Understanding The Five Essential Stages of Cyber Security helps businesses build comprehensive defenses, ensuring long-term security and success.



