In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, understanding the 7 layers of cybersecurity is essential for both businesses and individuals. This framework provides a systematic approach to organizing security measures, ensuring that all potential vulnerabilities are addressed effectively. Here’s an overview of each layer and its significance in strengthening your cybersecurity posture.

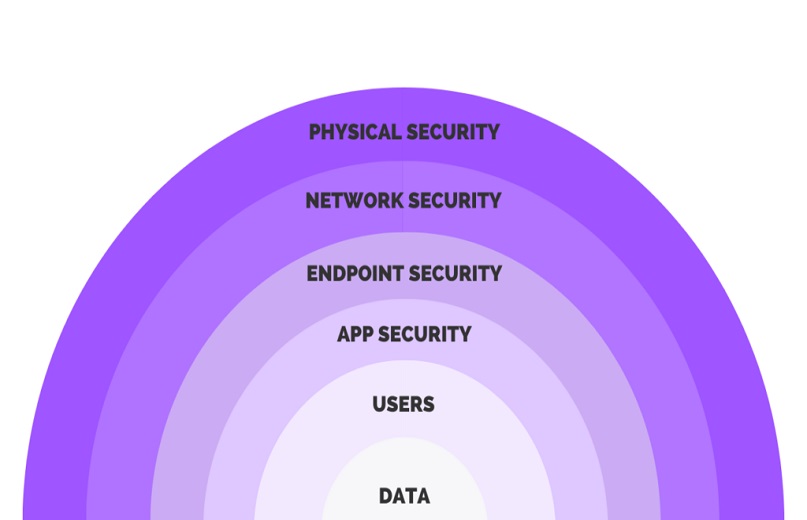
Overview of the 7 Layers of Cybersecurity
The 7 layers of cybersecurity encompass various protective measures that work together to create a comprehensive defense against cyber threats. By addressing each layer, organizations can enhance their overall security posture and better protect sensitive information.
1. Physical Security
The first layer of cybersecurity focuses on protecting the physical assets of an organization. It safeguards hardware, servers, and data centers from unauthorized access, theft, or damage. Key physical security measures include:
- Access control systems (e.g., keycards, biometric scanners)
- Surveillance cameras
- Security personnel
- Environmental controls (e.g., fire suppression, temperature monitoring)
2. Network Security
Network security is crucial for protecting the integrity, confidentiality, and availability of data and resources within a network. This layer employs various technologies and processes to defend against unauthorized access and cyberattacks. Key components include:
- Firewalls to block unauthorized traffic
- Intrusion detection systems (IDS) to monitor suspicious activity
- Virtual private networks (VPNs) for secure remote access
- Network segmentation to limit the impact of potential breaches
3. Endpoint Security
As mobile devices and remote work become more prevalent, endpoint security is increasingly vital. This layer focuses on securing individual devices such as computers, smartphones, and tablets. Effective strategies include:
- Antivirus and anti-malware software
- Device encryption
- Regular software updates and patch management
- Mobile device management (MDM) solutions
4. Application Security
Applications are significant entry points for cyber threats. Application security aims to protect software applications from vulnerabilities and attacks. This layer encompasses:
- Secure coding practices during development
- Regular security testing (e.g., penetration testing, code reviews)
- Application firewalls to filter and monitor HTTP traffic
- Ongoing monitoring for vulnerabilities post-deployment
5. Data Security
Given that data is one of the most valuable assets for any organization, data security is a critical layer. This involves protecting sensitive information from unauthorized access and breaches through:
- Data encryption both at rest and in transit
- Access controls to limit who can view or modify data
- Data loss prevention (DLP) solutions to detect and respond to potential breaches
- Regular data backups and recovery plans
6. Identity and Access Management (IAM)
Identity and Access Management (IAM) ensures that the right individuals have access to the right resources at the right times. This layer involves:
- User authentication methods (passwords, multi-factor authentication)
- Role-based access control (RBAC) to limit access based on job functions
- Identity verification processes
- Continuous monitoring of user activities to detect anomalies
7. Security Awareness Training
The final layer emphasizes the importance of educating employees about cybersecurity threats and best practices. Human error is often the weakest link in cybersecurity. Effective training can mitigate risks through:
- Regular training sessions on recognizing phishing attempts and social engineering attacks
- Providing resources and guidelines for secure online behavior
- Encouraging a culture of security awareness within the organization
- Simulating attacks to prepare employees for real-world scenarios
Conclusion
Understanding the 7 layers of cybersecurity provides a comprehensive approach to safeguarding an organization’s digital assets. By implementing robust measures across all layers—from physical security to security awareness training—organizations can create a multi-faceted defense strategy against the evolving landscape of cyber threats. Regular assessments and updates to these layers will ensure that cybersecurity remains a priority, adapting to new challenges as they arise. Investing in the 7 layers of cybersecurity is essential for protecting your organization’s valuable information and maintaining a strong security posture.